Chicago RCFL


The Chicago Regional Computer Forensics Laboratory (RCFL) provides assistance to law enforcement agencies with jurisdiction in northern Illinois. The Local Executive Board has authorized the RCFL Director to accept significant cases from any agency in the service area. The Chicago RCFL service area is represented by the 18 counties listed below and is highlighted in white on the map of Illinois:
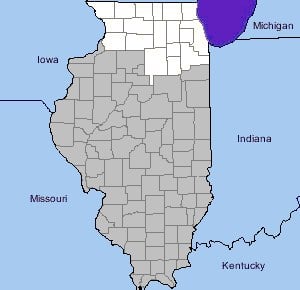
- Boone
- Carroll
- Cook
- DeKalb
- DuPage
- Grundy
- JoDaviess
- Kane
- Kendall
- Lake
- LaSalle
- Lee
- McHenry
- Ogle
- Stephenson
- Whiteside
- Will
- Winnebago
Participating Agencies
The Chicago RCFL is a unique partnership that promotes quality and strengthens computer forensics capacity. Computer forensics professionals from the following organizations are currently staffing the RCFL:
